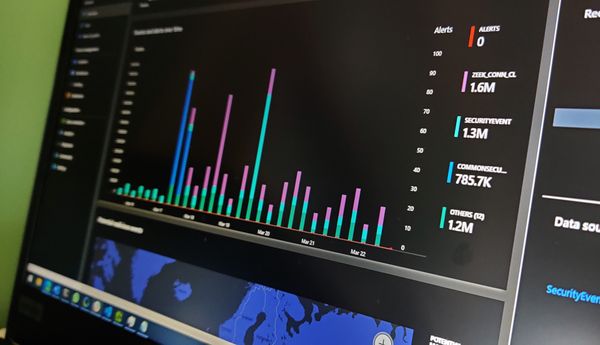
Integrating Canary Tokens with Microsoft Sentinel

For anyone not familiar with Canary Tokens - it's a free service offered by Thinkst which allows for the creation of various kinds of token that can be hidden in a environment ready to be tripped by an attacker. They also offer a commercial service where canaries are deployed as virtual/physical appliances.
Canary tokens can be configured to send emails when they are triggered which is useful for starting out with a couple of tokens, however when you want to scale out, integration with existing security tools is really helpful. You could even automate an initial response to a token triggering with SIEM/SOAR tooling.
How to setup
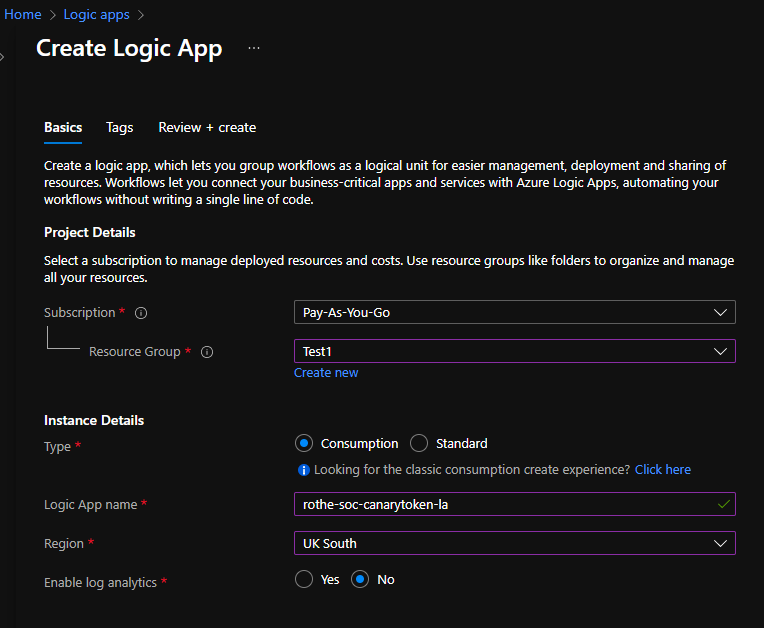
1) Create a new Azure Logic App, if you want more information on this process then the Microsoft documentation is worth a read, but it should probably look something like this
2) Start creating the logic-app based on the When an HTTP request is received.
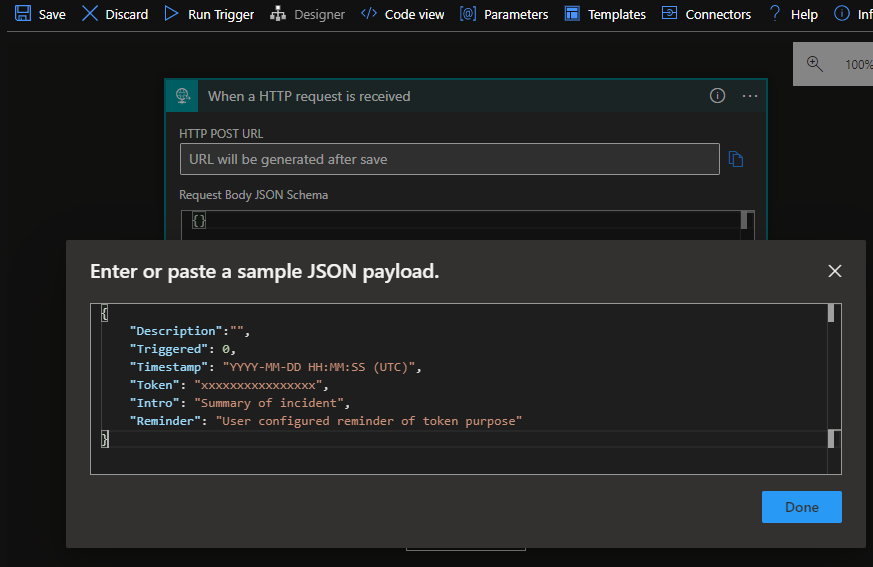
3) The HTTP Request trigger will now want a JSON schema to parse the incoming webhook data. To simply submit all of the incoming data directly, we don't need to worry about getting this correct. However it does mean we can add filters/conditionals etc. later
A sample of the data is published in the Thinkst documentation
{
"Description":"Type of Token",
"Triggered": 0,
"Timestamp": "YYYY-MM-DD HH:MM:SS (UTC)",
"Token": "xxxxxxxxxxxxxxxx",
"Intro": "Summary of incident",
"Reminder": "User configured reminder of token purpose"
}We can ask Azure to use this sample data to produce a schema
Which should then look like this
{
"type": "object",
"properties": {
"Description": {
"type": "string"
},
"Triggered": {
"type": "integer"
},
"Timestamp": {
"type": "string"
},
"Token": {
"type": "string"
},
"Intro": {
"type": "string"
},
"Reminder": {
"type": "string"
}
}
}4) Now that the logic-app can parse the incoming webhook, we need to add an action for it to send the data into Azure Sentinel. This requires the Log Analytics Data Collector connector and the Send Data action
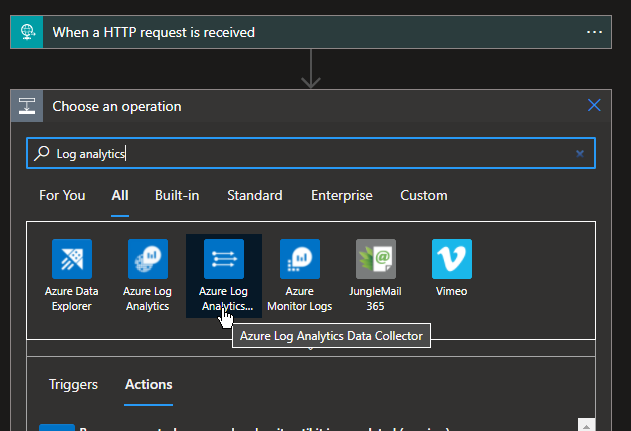
If you haven't previously used this connector to send data into Log Analytics then you'll be prompted to create a new connection with the workspace details
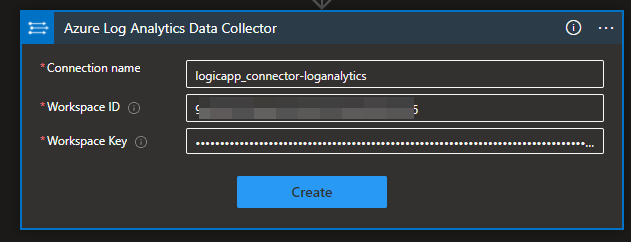
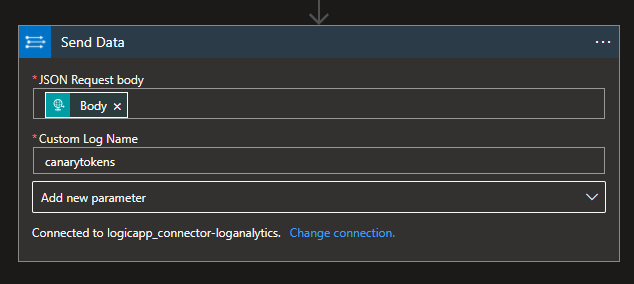
5) We are now asked for a JSON string to send into Log Analytics, we could build this from the fields defined above or just select the raw JSON that's submitted as per this screenshot. We also need to specify the name of the table to store the data
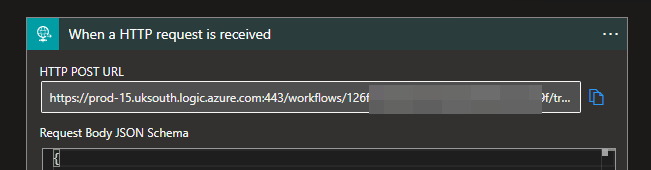
6) Once you save the app, the HTTP trigger will generate a unique URL, grab a copy of this
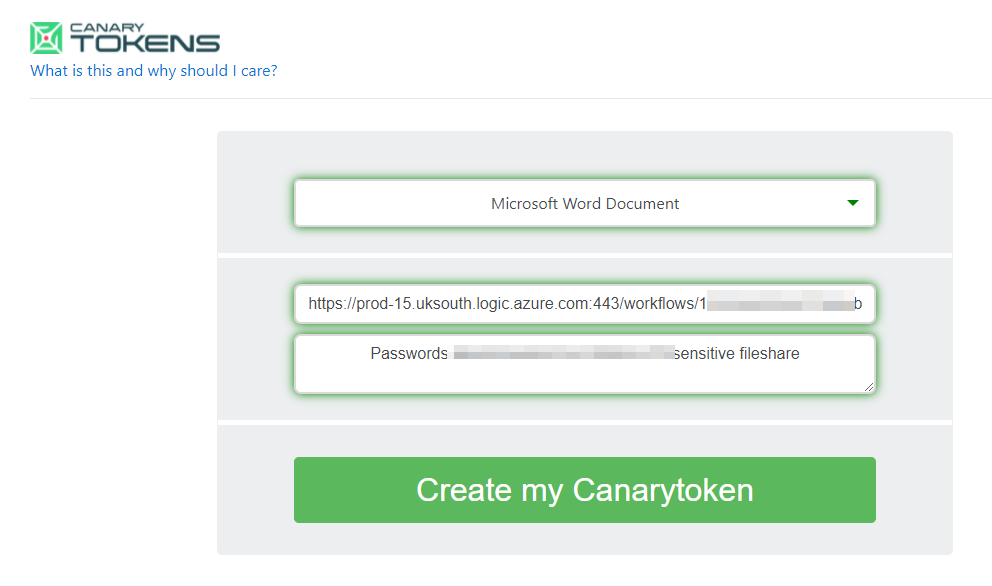
7) Now we can create a Canary Token of any kind, I'm choosing an Word Document that can be given an enticing name like passwords.docx and left on a file-share that shouldn't normally be accessed.
Paste the log-app URL into the webhook field and enter a sensible name.
Once you've created the token, you'll be able to download the document.
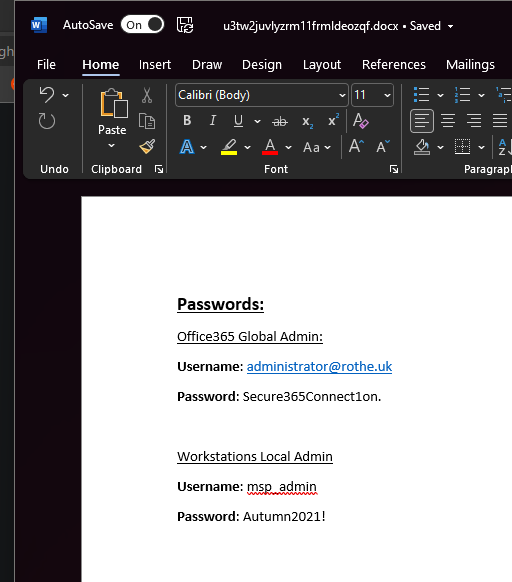
You might want to include some fake password data inside the document so that an attacker is less suspicious when they open the file.
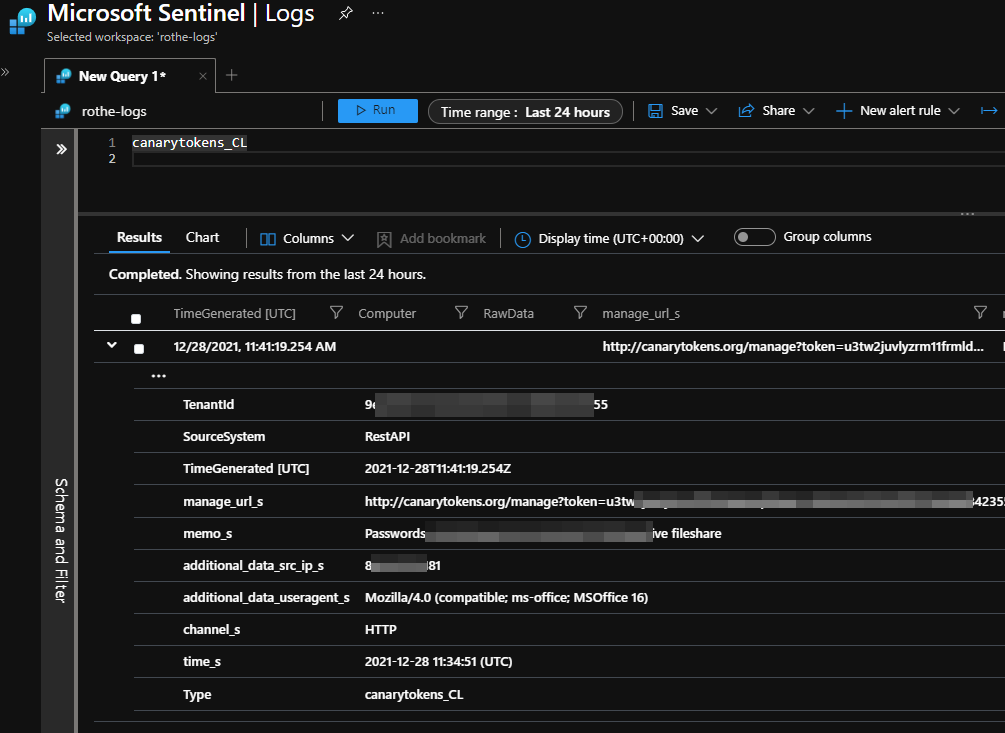
8) Once you open up the document you should very quickly see an entry in Log Analytics with all of the details
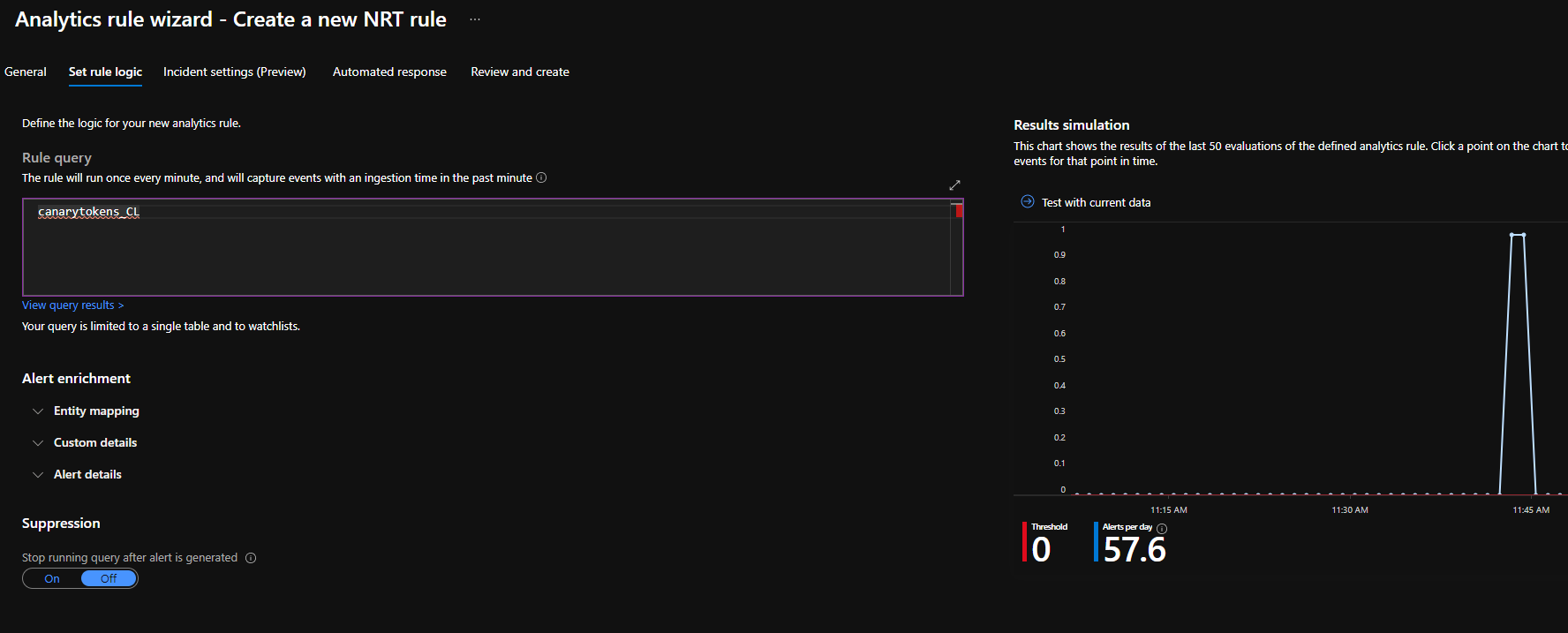
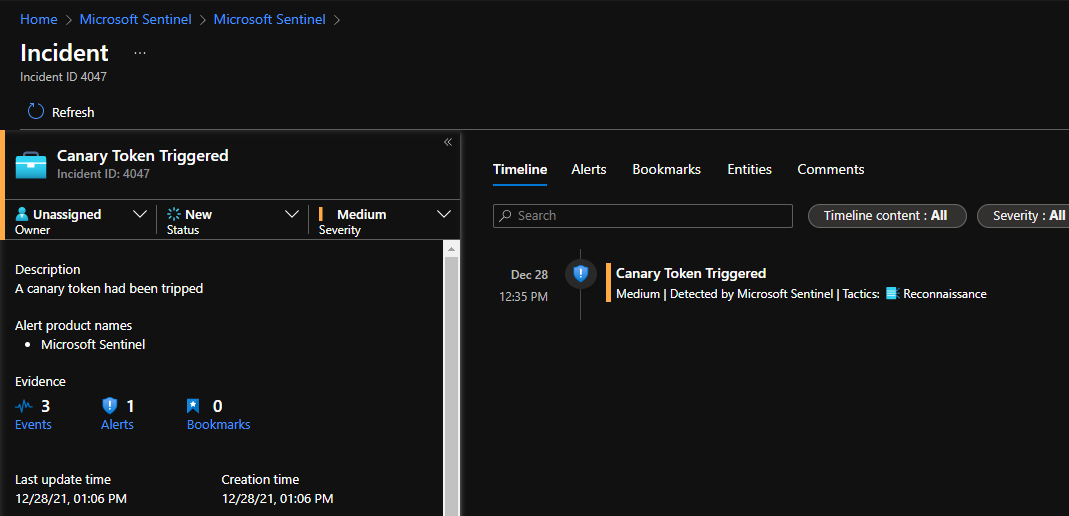
9) If you want alerts when the token is triggered you can add an analytics rule, in this case I'm using an NRT (near-real-time) rule